Advertisements
Advertisements
What is Data and Information?
Concept: undefined > undefined
Give examples of data and information.
Concept: undefined > undefined
Advertisements
Tick the appropriate circle.
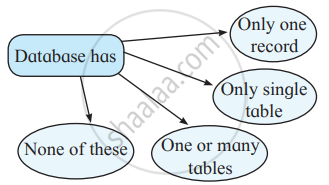
Concept: undefined > undefined
What is a database?
Concept: undefined > undefined
Explain functional units of a computer system.
Concept: undefined > undefined
Solve the following puzzles.
Fill the blocks

Across
2. The tag used to create table row.
4. Tag to create a form
Down
1. The attribute used to specify the path of a linked document.
3. The tag used to display horizontal ruled line.
Concept: undefined > undefined
Solve the puzzle by finding words with the help of hint given below.
| p | z | c | b | e | p | e | s |
| r | l | o | m | v | d | l | l |
| s | k | n | s | a | r | s | t |
| y | e | f | a | l | s | e | d |
| w | q | i | s | n | a | n | g |
| v | a | r | o | s | d | y | z |
| i | l | m | e | n | c | x | i |
- Boolean value.
- Keyword used in conditional if statement.
- Built-In function in JavaScript
- Function to check given value is number or not
- Keyword used to declare variable
- Function used to evaluate given expression
Concept: undefined > undefined
Complete the following chart. Examples of unauthorized access

Concept: undefined > undefined
Fill following boxes with appropriate cyber crime name
Copyright violation of software created originally by an individual.
Concept: undefined > undefined
Fill following boxes with appropriate cyber crime name
Gaining access without the user’s permission.
Concept: undefined > undefined
Fill following boxes with appropriate cyber crime name
Extracting confidential information by email.
Concept: undefined > undefined
Read the following and answer the question.
Rahul lost his pen drive in his college computer lab. His classmate Madhav finds it .He carries it home to return it to him the next day. When Madhav opens it he finds his favourite game. He thinks of making a duplicate copy of the game software.
- Does Madhav think ethically?
- What do you think should Madhav do?
- If he makes a duplicate copy then which cyber crime will he commit?
Concept: undefined > undefined
Explain three examples related to unauthorized access?
Concept: undefined > undefined
What are the advantages of a DBMS?
Concept: undefined > undefined
Tick whichever box is not valid.
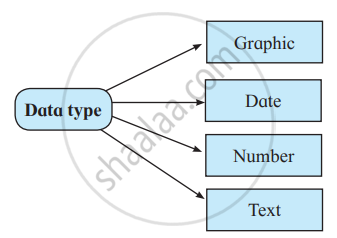
Concept: undefined > undefined
Student wants to create a field pincode in a table, which data type he will choose?
Concept: undefined > undefined
Observe the field names of a database given below in ‘Column A’ related to Bus reservation. Write suitable data types for each field in front of the respective field in ‘Column B’.
| Column A (Field Name) |
Column B (Data Type) |
| Passenger Name | |
| Age | |
| Gender | |
| Mobile Number |
Concept: undefined > undefined
In a company the data is stored in a table under the following fields Employee number, Last name, Date of birth, Address. Which data type will you use for the above field.
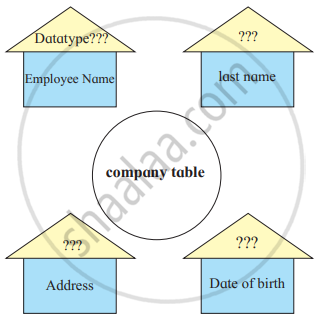
Concept: undefined > undefined
