Advertisements
Online Mock Tests
Chapters
![NCERT solutions for Computer Science [English] Class 11 chapter 11 - Societal Impact NCERT solutions for Computer Science [English] Class 11 chapter 11 - Societal Impact - Shaalaa.com](/images/computer-science-english-class-11_6:f845d20929ea4abdb3a8e0cf9f430d7f.jpg)
Advertisements
Solutions for Chapter 11: Societal Impact
Below listed, you can find solutions for Chapter 11 of CBSE NCERT for Computer Science [English] Class 11.
NCERT solutions for Computer Science [English] Class 11 11 Societal Impact Exercise [Pages 245 - 250]
After practicals, Atharv left the computer laboratory but forgot to sign off from his email account. Later, his classmate Revaan started using the same computer. He is now logged in as Atharv. He sends inflammatory email messages to few of his classmates using Atharvs email account. Revaans activity is an example of which of the following cybercrime? Justify your answer.
Hacking
Identity theft
Cyber bullying
Plagiarism
Rishika found a crumpled paper under her desk. She picked it up and opened it. It contained some text which was struck off thrice. But she could still figure out easily that the struck-off text was the email ID and password of Garvit, her classmate. What is ethically correct for Rishika to do?
Inform Garvit so that he may change his password.
Give the password of Garvit’s email ID to all other classmates.
Use Garvit’s password to access his account.
Suhana is down with fever. So, she decided not to go to school tomorrow. Next day, in the evening she called up her classmate, Shaurya and enquired about the computer class. She also requested him to explain the concept. Shaurya said, "Mam taught us how to use tuples in python". Further, he generously said, "Give me some time, I will email you the material which will help you to understand tuples in python". Shaurya quickly downloaded a 2-minute clip from the Internet explaining the concept of tuples in python. Using video editor, he added the text "Prepared by Shaurya" in the downloaded video clip. Then, he emailed the modified video clip to Suhana. This act of Shaurya is an example of:
Fair use
Hacking
Copyright infringement
Cyber crime
After a fight with your friend, you did the following activities. Which of these activities is not an example of cyber bullying?
You sent an email to your friend with a message saying that “I am sorry”.
You sent a threatening message to your friend saying “Do not try to call or talk to me”.
You created an embarrassing picture of your friend and uploaded on your account on a social networking site.
None of the above
Sourabh has to prepare a project on “Digital India Initiatives”. He decides to get information from the Internet. He downloads three web pages (webpage 1, webpage 2, webpage 3) containing information on Digital India Initiatives. Which of the following steps taken by Sourabh is an example of plagiarism or copyright infringement? Give justification in support of your answer.
- He read a paragraph on “ Digital India Initiatives” from webpage 1 and rephrased it in his own words. He finally pasted the rephrased paragraph in his project.
- He downloaded three images of “ Digital India Initiatives” from webpage 2. He made a collage for his project using these images.
- He downloaded the “Digital India Initiative” icon from web page 3 and pasted it on the front page of his project report.
Match the following:
| Column A | Column B |
| Plagiarism | Fakers, by offering special rewards or money prizes asked for personal information, such as bank account information. |
| Hacking | Copy and paste information from the Internet into your report and then organize it. |
| Credit card fraud | The trail is created when a person uses the Internet. |
| Digital Foot Print | Breaking into computers to read private emails and other files. |
You got the below-shown SMS from your bank querying a recent transaction. Answer the following:

Will you SMS your pin number to the given contact number?
You got the below-shown SMS from your bank querying a recent transaction. Answer the following:

Will you call the bank helpline number to recheck the validity of the SMS received?
Preeti celebrated her birthday with her family. She was excited to share the moments with her friend Himanshu. She uploaded selected images of her birthday party on a social networking site so that Himanshu can see them. After a few days, Preeti had a fight with Himanshu. The next morning, she deleted her birthday photographs from that social networking site, so that Himanshu cannot access them. Later in the evening, to her surprise, she saw that one of the images which she had already deleted from the social networking site was available with their common friend Gayatri. She hurriedly enquired Gayatri “Where did you get this picture from?”. Gayatri replied, “Himanshu forwarded this image a few minutes back”.
Help Preeti to get answer to the following question. Give justification for your answer so that Preeti can understand them clearly.
How could Himanshu access an image which I had already deleted?
Preeti celebrated her birthday with her family. She was excited to share the moments with her friend Himanshu. She uploaded selected images of her birthday party on a social networking site so that Himanshu can see them. After a few days, Preeti had a fight with Himanshu. The next morning, she deleted her birthday photographs from that social networking site, so that Himanshu cannot access them. Later in the evening, to her surprise, she saw that one of the images which she had already deleted from the social networking site was available with their common friend Gayatri. She hurriedly enquired Gayatri “Where did you get this picture from?”. Gayatri replied, “Himanshu forwarded this image a few minutes back”.
Help Preeti to get the answer to the following question. Give justification for your answer so that Preeti can understand them clearly.
Can anybody else also access these deleted images?
Preeti celebrated her birthday with her family. She was excited to share the moments with her friend Himanshu. She uploaded selected images of her birthday party on a social networking site so that Himanshu can see them. After a few days, Preeti had a fight with Himanshu. The next morning, she deleted her birthday photographs from that social networking site, so that Himanshu cannot access them. Later in the evening, to her surprise, she saw that one of the images which she had already deleted from the social networking site was available with their common friend Gayatri. She hurriedly enquired Gayatri “Where did you get this picture from?”. Gayatri replied, “Himanshu forwarded this image a few minutes back”.
Help Preeti to get the answer to the following question. Give justification for your answer so that Preeti can understand them clearly.
Had these images not been deleted from my digital footprint?
The school offers a wireless facility (wifi) to the Computer Science students of Class XI. For communication, the network security staff of the school has a registered URL schoolwifi.edu. On 17 September 2017, the following email was mass distributed to all the Computer Science students of Class XI. The email claimed that the password of the students was about to expire. Instructions were given to go to the URL to renew their password within 24 hours.

Do you find any discrepancy in this email?
The school offers a wireless facility (wifi) to the Computer Science students of Class XI. For communication, the network security staff of the school has a registered URL schoolwifi.edu. On 17 September 2017, the following email was mass distributed to all the Computer Science students of Class XI. The email claimed that the password of the students was about to expire. Instructions were given to go to the URL to renew their password within 24 hours.

What will happen if the student will click on the given URL?
The school offers a wireless facility (wifi) to the Computer Science students of Class XI. For communication, the network security staff of the school has a registered URL schoolwifi.edu. On 17 September 2017, the following email was mass distributed to all the Computer Science students of Class XI. The email claimed that the password of the students was about to expire. Instructions were given to go to the URL to renew their password within 24 hours.

Is email an example of cybercrime? If yes, then specify which type of cybercrime is it. Justify your answer.
You are planning to go on a vacation. You surfed the Internet to get answers to the following queries:
- Weather conditions
- Availability of air tickets and fares
- Places to visit
- Best hotel deals
How would you recognize if one of your friends is being cyberbullied?
Cite the online activities which would help you detect that your friend is being cyberbullied.
How would you recognize if one of your friends is being cyberbullied?
What provisions are in the IT Act 2000, (amended in 2008) to combat such situations?
Write the difference between the following -
Copyrights and Patents
Write the difference between the following -
Plagiarism and Copyright infringement
Write the difference between the following -
Non-ethical hacking and Ethical hacking
Write the difference between the following -
Active and Passive footprints
Write the difference between the following -
Free software and Free and open-source software
If you plan to use a short text from an article on the web, what steps must you take in order to credit the sources used?
When you search online for pictures, how will you find pictures that are available in the free public domain? How can those pictures be used in your project without copyright violations?
Describe why it is important to secure your wireless router at home. Search the Internet to find the rules to create a reasonably secure password. Create an imaginary password for your home router. Will you share your password for the home router with the following people? Justify your answer.
- Parents
- Friends
- Neighbours
- Home Tutors
List down the steps you need to take in order to ensure -
your computer is in good working condition for a longer time.
List down the steps you need to take in order to ensure -
smart and safe Internet surfing.
What is data privacy?
Websites that you visit collect what type of information about you?
In the computer science class, Sunil and Jagdish were assigned the following task by their teacher.
- Sunil was asked to find information about “India, a Nuclear power”. He was asked to use the Google Chrome browser and prepare his report using Google Docs.
- Jagdish was asked to find information about “Digital India”. He was asked to use the Mozilla Firefox browser and prepare his report using Libre Office Writer.
What is the difference between the technologies used by Sunil and Jagdish?
Cite examples depicting that you were a victim of the following cybercrime. Also, cite provisions in IT Act to deal with such a cybercrime.
Identity theft
Cite examples depicting that you were a victim of the following cybercrime. Also, cite provisions in IT Act to deal with such a cybercrime.
Credit card account theft
Neerja is a student of Class XI. She has opted for Computer Science. Neerja prepared the project assigned to her. She mailed it to her teacher. The snapshot of that email is shown below.
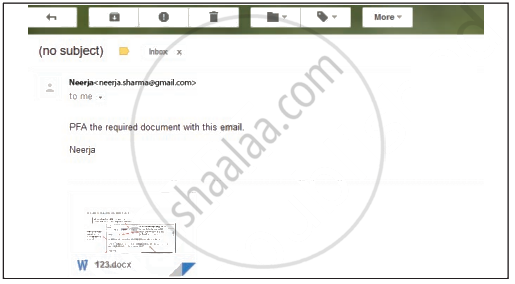
Find out which of the following email etiquettes are missing in it. Justify your answer.
- The subject of the mail
- Formal greeting
- Self-explanatory terms
- Identity of the sender
- Regards
Sumit got good marks in all the subjects. His father gifted him a laptop. He would like to make Sumit aware of health hazards associated with the inappropriate and excessive use of laptops. Help his father to list the points which he should discuss with Sumit.
Solutions for 11: Societal Impact
![NCERT solutions for Computer Science [English] Class 11 chapter 11 - Societal Impact NCERT solutions for Computer Science [English] Class 11 chapter 11 - Societal Impact - Shaalaa.com](/images/computer-science-english-class-11_6:f845d20929ea4abdb3a8e0cf9f430d7f.jpg)
NCERT solutions for Computer Science [English] Class 11 chapter 11 - Societal Impact
Shaalaa.com has the CBSE Mathematics Computer Science [English] Class 11 CBSE solutions in a manner that help students grasp basic concepts better and faster. The detailed, step-by-step solutions will help you understand the concepts better and clarify any confusion. NCERT solutions for Mathematics Computer Science [English] Class 11 CBSE 11 (Societal Impact) include all questions with answers and detailed explanations. This will clear students' doubts about questions and improve their application skills while preparing for board exams.
Further, we at Shaalaa.com provide such solutions so students can prepare for written exams. NCERT textbook solutions can be a core help for self-study and provide excellent self-help guidance for students.
Concepts covered in Computer Science [English] Class 11 chapter 11 Societal Impact are Intellectual Property Right, Software Licensing, Digital Technologies, Digital Footprints, Digital Society and Netizen, Data Protection, Cyber Crimes, Indian Information Technology Act (IT Act), Impact on Health, Violation of Intellectual Property Right (IPR), Public Access and Open Source Software.
Using NCERT Computer Science [English] Class 11 solutions Societal Impact exercise by students is an easy way to prepare for the exams, as they involve solutions arranged chapter-wise and also page-wise. The questions involved in NCERT Solutions are essential questions that can be asked in the final exam. Maximum CBSE Computer Science [English] Class 11 students prefer NCERT Textbook Solutions to score more in exams.
Get the free view of Chapter 11, Societal Impact Computer Science [English] Class 11 additional questions for Mathematics Computer Science [English] Class 11 CBSE, and you can use Shaalaa.com to keep it handy for your exam preparation.
