Topics
Number Systems
Program Analysis
Introduction to C+ +
- Introduction to C++
- Character Sets
- Standard I/O Strems in C++
- Type Modifiers
- C++ Data Types
- Variables in C++
- Constants
- Compiler Tokens
- Operators in C++
- Comments in C++
- Scope and Visibility
- Control Statements
- Functions in C++
- Default Arguments
- Techniques used to pass Variables into C++ Functions
- Function Overloading
- Inline Functions
- Recursion
- Pointers in C++
- Arrays in C++
- References
- Type Conversion in Expressions
Visual Basic
- Introduction to Visual Basic
- One language Three Editions
- Study Of Integrated Development Environment (IDE)
- Visual Basic Programming
- Few Common Methods
Introduction to Networking and Internet
- Introduction to Networking and Internet
- Networking Terms and Concepts
- Types of Networks
- Network Security
- Network Configurations
- Network Applications
Networking Terms and Concepts
Introduction
Networking involves sharing resources and services. A computer network consists of interconnected systems using a shared communication link. Systems connect through a transmission medium and follow common communication rules, called protocols, to ensure data reaches its destination and systems understand each other.
What does networking allows to do?
- Exchanging Information: Connected computers can quickly and easily transfer information between each other.
- Sharing Hardware Resources: A network allows shared use of hardware like printers and drives, reducing hardware costs.
- Preserving Information: Information is stored on a specific device in the network and can be accessed by authorized users.
- Protecting Information: Information is safeguarded from unauthorized access, maintaining privacy and security.
Types of network installations
Note:
- Centralized installation: These networks have a central mainframe computer connected to all other computers, known as dumb terminals or nodes, which serve only as input/output devices.
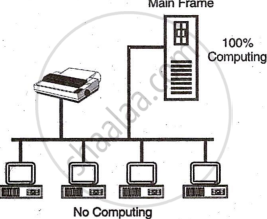
- Distributed installation: In a distributed network, each node processes data independently due to the high processing capacity and memory of modern PCs. This approach enhances efficiency by processing more data in less time.
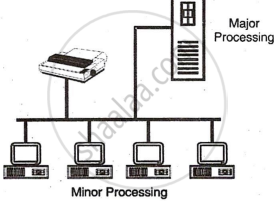
- Collaborative installation: Also known as cooperative processing, this method allows computers to share data, resources, and services collaboratively. Applications execute more efficiently within the network by utilising available resources.
Network Security
Network security involves both software and hardware issues. Software security concerns unauthenticated access to programs, which can lead to data loss or damage if not properly managed. Effective techniques must be implemented to prevent these problems. Hardware security ensures that unauthorized individuals cannot access network resources like floppy drives, hard disks, and CD drives. The operating system should enforce appropriate policies to address these issues.
Network Configurations
Note: Network configuration means the method of operating a network by deciding the node authorities. There are two basic configurations generally found in many organization:
- Client-Server: A high-performance PC (called server) provides services and resources to multiple users (clients) in the network. Example: Novell Netware.
- Peer-to-Peer: Each PC has equal rights, directly communicating without a server. Example: Windows 95, Windows NT workstations.
